Trust me! Trustworthiness is more important than ever
October 8, 2022 was a black day for rail passengers. A targeted attack on the rail communications infrastructure paralyzed operations in several German states for a good three hours and led to disruptions in the timetable that lasted for days. This event impressively demonstrates how vulnerable our everyday lives are to disruptions in information and communications technology. But not all disruptions are so obvious. Many attacks happen in secret and are not limited to software either. Rather, nowadays far-reaching gateways already exist at the hardware level of electronic systems.
Against the backdrop of the ever-increasing penetration of electronics in all areas of life, it is worth taking a deeper look at the topic. Today, smart systems can be found everywhere: in machines, on or in clothing, in buildings or vehicles of all kinds, in medical devices or even in infrastructure. Everywhere where it is a matter of recording measured values, digitizing them, processing them into information and communicating them. And everywhere there is a high demand for trustworthiness. Companies must be able to trust that data from production will not be passed on to third parties without control. Private individuals must be able to trust that household appliances etc. are not spying on them. Traffic participants must be able to trust that they will not be harmed by undesirable vehicle behavior. And patients must be able to trust that no one can cause malfunctions in medical devices.
These examples already show that trustworthiness has numerous facets. It is not just a matter of information security in the sense of availability, confidentiality and integrity. Rather, aspects such as functional safety, protection against the theft of intellectual property and protection against manipulation of (both safety- and security-relevant) functions also play an essential role. In this context, it is not enough to focus on the software; the entire value chain from semiconductor manufacturing to the system level must be included in the consideration.
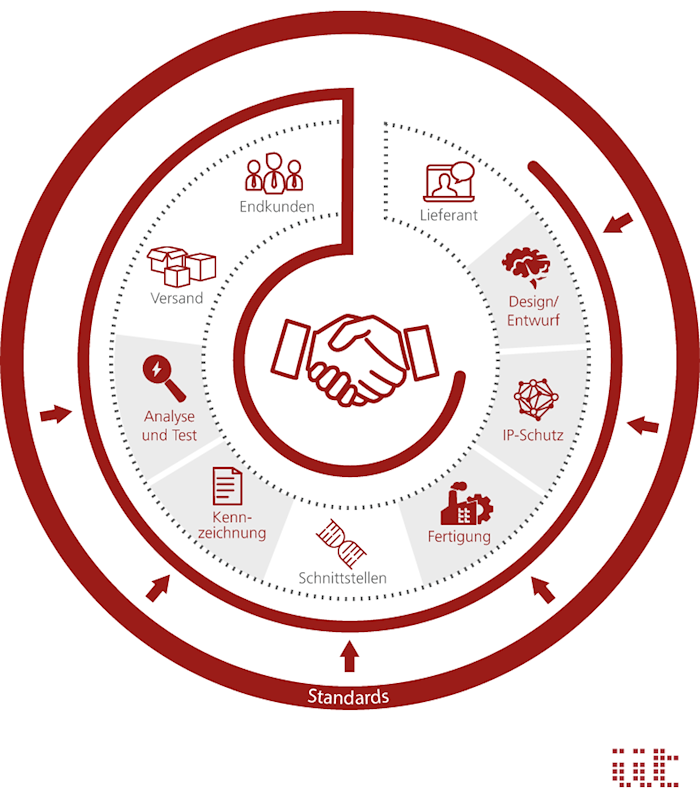
Trustworthiness along the value chain. | Image: iit, Berlin
Trustworthiness is functional safety
Attacks or manipulations are not always at the core of trustworthiness. The aspect of functional safety must not be neglected either. In view of the increasingly far-reaching decision-making autonomy of electronic systems – whether in cooperation between humans and robots, in autonomous driving or even in medical technology – it is becoming increasingly important for end users to be able to rely on the proper functioning of robots, vehicles or other products. This means that the systems must detect functional errors and, if necessary, go into a safety mode that does not endanger anyone. However, this aspect is not the focus of the article.
Trustworthiness is protection of intellectual property
When it comes to trust, the authenticity of products also plays a particularly important role. Product counterfeiting is a significant problem in the electronics industry along the entire value chain. Even chips are counterfeited! Counterfeits are often significantly cheaper than the originals, but the quality is often correspondingly poorer, i.e. the product properties do not meet expectations. In the case of safety-relevant components, there is a risk that failures will occur in the event of a fault or in the critical marginal areas of the specifications, resulting in danger or damage. Traceability and identification possibilities through certificates of authenticity are therefore an important element of trustworthiness, but this is also not the focus of this article.
Trustworthiness affects the entire value chain
This already starts with chip design. Typically, chips are not developed from scratch, but are based on IP blocks for common functions. These are extended to include specific functions. The IP blocks are purchased and cannot be tested down to the last detail due to their high complexity.
This is already the first gateway. It is quite possible to replace one or more IP blocks with ones that contain undesirable functions, e.g., for eavesdropping and forwarding data traffic, granting access rights to data that is actually protected, or even manipulating the desired functionality. On the other hand, attackers can tap chip designs along the path from designer to semiconductor manufacturer and directly determine how the chips work. Each of these scenarios has a high threat potential. At the same time, it is extremely difficult to detect such manipulations.
Nowadays, electronic assemblies are sometimes more complex and more highly integrated than chips were a few decades ago. Here, too, it is comparatively easy to exchange components for manipulated versions or to add additional components that allow attackers far-reaching control. Due to their extremely small size, such “additions” can only be found by intensive inspection of the assemblies.
However, even electronic systems that have not been tampered with can be attacked at the hardware level, especially with physical access. A classic way is the “reverse engineering” of chips. This involves opening the encapsulation and removing it layer by layer. For each layer, the circuit topology is recorded and, at the end, assembled into an overall picture. By “listening” to the signals running into or out of a chip during control operation, it is possible to tap the flowing data. Another possibility is to inject targeted signals into the chip and analyze the behavior or the output signals. In addition to the loss of confidentiality of the data, these methods make it possible above all to draw conclusions about how chips work. In other words, intellectual property is attacked. This is particularly important in the case of ASICs. After all, a significant part of the value creation there is in the algorithms, which are thus disclosed.
Last but not least, the software must meet trustworthiness requirements. While direct access to the hardware is often not so easy, software systems offer significantly more attack surface for external access. Accordingly, there are countless attack vectors and just as many concepts for safeguarding against cyber attacks. Software, on the other hand, is comparatively easy to adapt and improve through updates. With hardware, this is much more difficult and only possible by physically replacing components. However, both sides must always be considered equally.
Trustworthiness is a current research topic
Of course, the attack vectors mentioned above are by no means unknown. Many research groups are working on solutions to close these gateways.
The obvious measure for identifying manipulations as well as functional errors is intensive testing of chips, assemblies and systems. However, in view of the great variety, large quantities and extreme complexity of electronic products, this is only partially effective. It is almost impossible for an electrical or visual test to capture all possibilities for tampering or defects. Therefore, new test and analysis methods are the subject of intensive research.
Chip designers can plan additional IP blocks without a function or create particularly complicated signal paths as early as the design phase. This procedure is intended to conceal the actual functions and make it more difficult to steal intellectual property (obfuscation). However, this increases both the development effort and the chip area and thus the cost. In addition, this type of protection offers only comparatively low security.
A newer approach is to use reconfigurable transistors to determine the functions only at runtime, quasi “by software”. If an attacker were to determine the layout, he would not be able to infer the functionality. The VE-CirroStrato project, which is funded by the German Federal Ministry of Education and Research (BMBF) and coordinated by NamLab gGmbH, has set itself precisely this goal.
The relatively new technology of chiplets also offers opportunities to increase trustworthiness. In this process, the chip is divided into subchips that contain different functional blocks. Manufacturing the subchips in different technologies or at different semiconductor manufacturers not only reduces costs, but also increases security. Particularly critical chiplets, for example, could be ordered from especially trustworthy manufacturers. An attacker would either have to compromise all semiconductor manufacturers or have in-depth knowledge of the structure and distribution of the chip’s functions in advance. Both increase the barrier to entry and thus security. The German Federal Ministry of Education and Research is funding research into appropriate protection mechanisms with VE-REWAL and VE-Jupiter.
In addition, chips can be protected against opening by incorporating mechanisms that ensure the destruction of critical parts of the chip and delete stored data (“tamper protection”) in the event of a breach of the integrity of the encapsulation. There are various approaches to this, but most of them are still being researched.
In the BMBF-funded VE-CeraTrust project, a consortium with partners from industry and science (including: VIA electronic GmbH, Hermsdorf; Fraunhofer Institute for Ceramic Technologies and Systems IKTS, Dresden) is investigating approaches to use multilayer ceramic systems to create new protection mechanisms for shielding and concealing as well as for the traceability of electronic assemblies.
Trustworthiness is a question of traceability
A chain is only as strong as its weakest link. This also applies to trustworthiness in electronics. It is not enough to become “secure” at one point; what is needed is a holistic approach. The interfaces between the stations in the value chain therefore play a key role in achieving trustworthy electronics. They ensure a strong connection between the links in the chain. Without standardization, however, these interfaces cannot be implemented in a practical manner.
Furthermore, trustworthiness must become verifiable. An end customer or user must be able to understand what the level of trustworthiness is and what measures have been taken to achieve it. Ultimately, some form of classification and certification is essential. These are also based on standards.
As part of the BMBF-funded VE-Velektronik project, a national platform is to be created to address overarching issues in the three pillars of design, manufacturing and analysis of the microelectronics value chain. Standardization, networking and the transfer of know-how will play a key role in this process.
Conclusion
Trustworthiness is a central aspect of electronics that is becoming increasingly important. The hardware as the foundation of the complex electronic system must be understood and manufactured in a trustworthy manner so that all subsequent levels, such as the security software, can perform their task properly. The entire chain from chip design to software system must be considered. And not just at the end of a development process, but from the beginning and accompanying it. Currently, there are numerous gaps in achieving trustworthiness. However, intensive research is being carried out to close these. With its flagship initiative “Vertrauenswürdige Elektronik” and the VE-Velektronik platform, the German Federal Ministry of Education and Research is bundling these activities to leverage synergy potential.
After all, only together and with the appropriate expertise can the players from Germany and Europe act globally on an equal footing and strengthen technological sovereignty. New standards and norms are being created for this purpose in cooperation with the European Commission and the European standardization authority CEN-CENELEC. At the same time, concerted action through trustworthy electronics “Made in Europe” offers the chance of new competitive advantages for the European electronics industry. The German government’s current Framework Program for Research and Innovation 2021 – 2024 “Mikroelektronik. Vertrauenswürdig und nachhaltig. Für Deutschland und Europa.” makes this one of the central tasks.
_ _ _ _ _
Authors of this article

Dr. Jochen Kerbusch
Electronics and Microsystems Division, Group Leader Technology Foresight, VDI/VDE-IT
E-mail: Jochen.kerbusch@vdivde-it.de
Phone: +49 351 486 797-37
and
Johannes Rittner
Senior Consultant, Electronics and Microsystems Division, VDI/VDE-IT
_ _ _ _ _
Further links
👉 VDI/VDE-IT Website
👉 Federal Ministry of Education and Research
👉 NamLab gGmbH